Strict Standards: Only variables should be assigned by reference in /home/noahjames7/public_html/modules/mod_flexi_customcode/tmpl/default.php on line 24
Strict Standards: Non-static method modFlexiCustomCode::parsePHPviaFile() should not be called statically in /home/noahjames7/public_html/modules/mod_flexi_customcode/tmpl/default.php on line 54
Strict Standards: Only variables should be assigned by reference in /home/noahjames7/public_html/components/com_grid/GridBuilder.php on line 29
iOS doesn’t need anti-virus software, right? I regularly receive email from security vendors, large and small, who insist that iOS will imminently be a hotbed of malware exploiting security holes—and that their software can help.
Of course, it can’t. iOS has had plenty of severe bugs discovered and patched. Just weeks ago, it came out in a security breach at a firm that specialized in helping governments peep in on targets (whether criminal or miscellaneous) that there were, in recent iOS releases, a number of targets.
And jailbreaking remains extant with a number of groups of varying degrees of trustworthiness distributing cracks that allow you to install anything you want, which includes anti-malware software, but also…malware. (Some jailbreaking advocates advocate using a reliable hack in order to plug holes used for jailbreaking, but there’s no way for normal users to determine which jailbreak hacks to trust.)
But Apple doesn’t give all apps the necessary permission to monitor and carry out tasks that would help prevent the installation and execution of software gone bad, nor track what it does and block or remove it if it crosses the line. We rely on Apple to make choices and respond to researchers and bug reports to prevent malware from getting close to installing. (iOS 9 included security fixes related to bypassing app security to install enterprise-certificate-signed apps, for instance.)
Content-blocking Safari extensions in iOS 9 could provide some actual assistance by preventing the most ready vector for exploits: subverted or malicious webpages. In iOS 9, a new Safari web controller allows apps from Apple and third parties to use a full-blown Safari browser inside an app. Previously, apps used a slightly stripped-down WebKit viewer instead. This allows not just Safari to run as an app to take advantage of blocking filters, but also any app that opens webpages in the Safari controller. Keeping Safari safe thus has a bigger impact than just launching the Safari app to browse.
Apple has a malicious website filter in iOS: In Settings > Safari, enable Fraudulent Website Warning, if it isn’t already. However, Apple doesn’t disclose how it assembles or updates the list it uses.
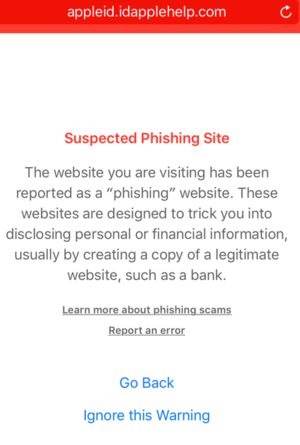
iOS warns you of suspected phishing sites, but who knows how Apple compiles the list?
Content filters can add protection against malware, because the app developers can use URL patterns to match and block entire malicious sites, plus scripts that are known to be malicious wherever they run, and media or other files named in a certain way. There’s a lot of good variation, and it’s possible to sidestep all of the issues associated with blocking ads or even protecting one’s privacy—the latter is a much more easily agreed-upon goal, even if content blockers don’t offer a clear path.
Developers don’t have to compile and maintain their own lists of bad actors. There are both free and collaborative lists—constantly updated—of both URLs and file names. One enterprising individual created a list of such lists.
Google’s Safe Browsing allows third parties to use the company’s extensive, up-to-date compendium of “suspected phishing, malware, and unwanted software pages.” Phishing pages pretend to be a legitimate site; malware tries to download or convince you to download it; and “unwanted software pages” are sites that push borderline malware to rack up affiliate revenue or page views.
Unfortunately, Google has just two paths into its database: as individual lookups, or as an encrypted downloadable database. The former won’t work, because Safari content-blocking filters have to be assembled before pages are loaded, and can’t be queried live. The latter won’t work, because it’s the same thing: a lookup of a page instead of a static page URL or pattern. The encryption allows Google to include URLs discovered by users who don’t want those URLs to be publicly exposed, but it also prevents creating filters.
There’s no requirement for content-blocking app developers to release their lists. 1Blocker does, and is so far unique in my testing: every item they block can be viewed via the app, and enabled or disabled separately.
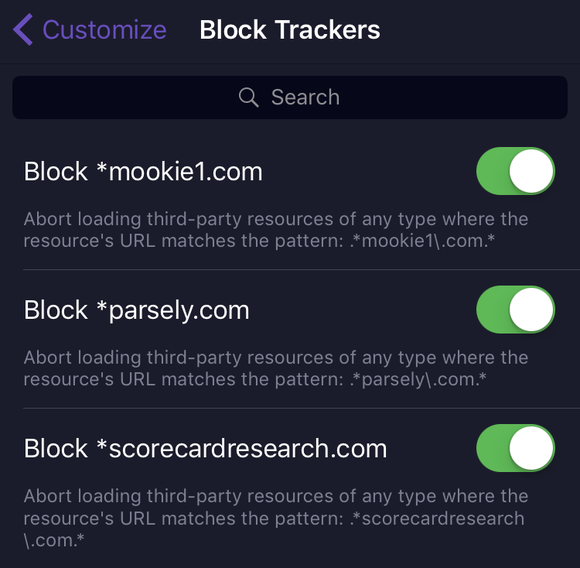
1Blocker exposes all the patterns they use to block sites and media.
But Google could conceivably create its own safe browsing app for iOS that took its safe-browsing list and packaging it for Safari’s consumption. The optics of that could be hilarious, too. Rather than complain about Apple allowing ad-blocking tools that squeeze Google’s mobile revenue, Google could provide a highly valuable, almost unique tool to prevent harm.
Don’t let the discussion around content-blocking extensions focus entirely on advertising and tracking. There’s a lot more of benefit and a lot more variety to come.
Strict Standards: Only variables should be assigned by reference in /home/noahjames7/public_html/modules/mod_flexi_customcode/tmpl/default.php on line 24
Strict Standards: Non-static method modFlexiCustomCode::parsePHPviaFile() should not be called statically in /home/noahjames7/public_html/modules/mod_flexi_customcode/tmpl/default.php on line 54
Find out more by searching for it!
