Strict Standards: Only variables should be assigned by reference in /home/noahjames7/public_html/modules/mod_flexi_customcode/tmpl/default.php on line 24
Strict Standards: Non-static method modFlexiCustomCode::parsePHPviaFile() should not be called statically in /home/noahjames7/public_html/modules/mod_flexi_customcode/tmpl/default.php on line 54
Strict Standards: Only variables should be assigned by reference in /home/noahjames7/public_html/components/com_grid/GridBuilder.php on line 29
Yahoo is trying something new: telling its users to bypass a password entirely in favor of a smartphone app through which a user grants access when a login is attempted. This seems like, in the words of one Twitter wit, two-factor authentication (2FA) with one factor. Is Yahoo’s Account Key offering a strange decision that will poorly affect the security of those with accounts in its network?
My straightforward answer is: No. Yahoo wants to make it easier for its users to have the benefits of authorized logins while reducing the utility of stolen passwords to bad actors, and it chose a method that’s better than passwords in nearly all circumstances. Strong words, I know! I don’t expect other companies to follow immediately, but Yahoo is trying to stand out.
It’s borrowing a page from more sophisticated systems, like Duo Security, which has a more complicated setup and is designed for corporate-scale security, but employs the same basic principles. Yahoo is bringing this idea to the masses who can use existing apps to take advantage.
The key factor is a lack of password
Let’s break down how its new Yahoo Account Key system works. I’ve tested it, and it works just like Yahoo says it should.
First, you install their new iOS app for Yahoo Mail. Account Key works just with this app and logging into Yahoo on the web, but will be rolling out to other apps this year, the company said in a blog post.
Next, log in with your username and password. You’re essentially turning the app into a trusted device—a la Apple’s old two-step and new two-factor systems—and thus you have to present current information. Next, tap the profile icon at the top of the screen and tap Settings. Tap Account Key and you can enable the service. Yahoo wisely walks you through a demo of accepting and rejecting connections so you can practice it. This is important for its target user for this feature.
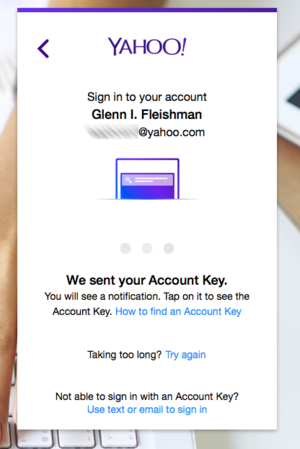
The Yahoo website passes the login approval to a smartphone app, offering alternatives if it doesn’t work. Once approved at the app, the login completes automatically.
In my test, I went to Yahoo.com to log into my email account. I entered the address, and it clearly immediately recognized I had Account Key active, as the password field changed to read Click to Use Account Key, and the Sign In button transformed to read Continue. A screen on the website says its waiting for approval, and your iOS device sends a notification that opens to a view that lets you agree to allow the log in or not.
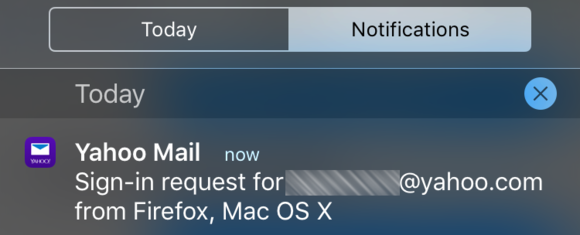
Login attempts show up as notificaitons if you’re not in the app.
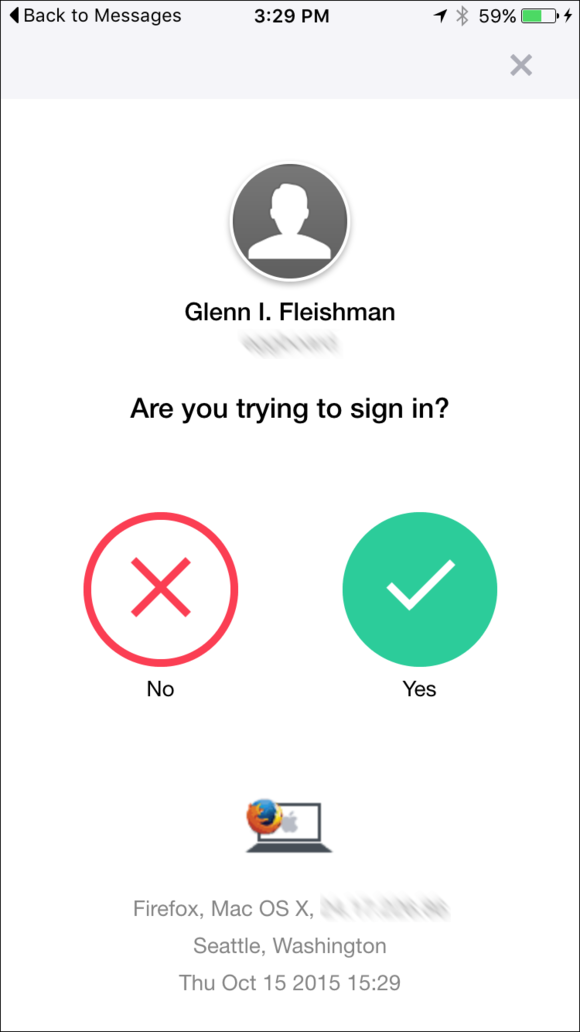
The Yahoo Mail app prompts you when a login attempt happens elsewhere. You’ve given a lot of contextual information and a big red X if it’s not ok.
To more experienced users, perhaps this all seems too trivial—how can this prevent a ne’er-do-well from accessing your account if all they need is your password to set up an iOS app? But the interplay is much richer than that.
True: You have to start by using an existing password. However, there’s no way to exploit this en masse. As with many kinds of account security issues, there’s a strong divide between being able to attack an individual target’s account (for theft, harassment, criminal evidence, and more) and having huge piles of passwords that can be used to attack giants wads of accounts.
I can get it for you wholesale
Yahoo turns a log in into a “retail” transaction, where someone has to obtain your account name and password, plug those into its app on an iOS or Android device, and have all the tracking associated with that.
Once past the login stage, not having a password is so much more secure than having a password for a large number of people. Normal human beings pick easy-to-remember passwords, which are in turn easily guessed or cracked. They also often provide passwords when phished through email or even grifted over the phone. Without a password, there’s nothing to steal—except the physical device on which the Account Key option is enabled.
This shifts the attack burden to physical proximity and personal knowledge. Someone who wants to break into your Yahoo email account can’t do so remotely: They have to be near you. They can’t do so quietly by just having access to your computer: They need your phone, and the phone has to be unlocked. If you have a passcode, they have to guess or know the passcode; with Touch ID, they need…one of your fingerprints. And they can’t do so without a trace: These connections are logged by time and date and IP address.
For a user who doesn’t want to compose difficult passwords and wants less risk of remote attack, Yahoo’s approach is frankly brilliant. It’s also just plain simpler than not just two-factor logins, but regular logins with passwords, which could lead to broad adoption by its users. It takes less time with a greater assurance and actuality of security. The bonus is that it makes any Yahoo security flubs less important, so long as the Account Key interaction is required for logins.
Now, some people want the extra security of a two-step or two-factor approach. In both cases, a password is still required, although it doesn’t have to be as strong as when used in isolation. A second step (approving a connection from a trusted device) or a second factor (a unique bit of information not available via the same login path). Apple’s new two-factor (but really two-step) system first asks your approval for a remote login by showing its rough location and requiring you click Allow (or Don’t Allow), before it gives you a code to use to supplement the password step.
Having two steps or factors combines something you know (the password), which might never be cracked or uncovered, with something else (a time-based one-time password, an SMS-delivered code, or something an app generates) that has to be obtained. But for most people, the gulf between what Yahoo is offering and a plain password is enormous, and a boost.
I’m looking forward to more straightforward variants on Yahoo’s scheme that shift cracking from global to physical proximity while also making it a better process for people who don’t want to manage their security, while still benefiting from it.
Strict Standards: Only variables should be assigned by reference in /home/noahjames7/public_html/modules/mod_flexi_customcode/tmpl/default.php on line 24
Strict Standards: Non-static method modFlexiCustomCode::parsePHPviaFile() should not be called statically in /home/noahjames7/public_html/modules/mod_flexi_customcode/tmpl/default.php on line 54
Find out more by searching for it!
